Proxy Write for us
A proxy server is a system or router that delivers a gateway between users and the internet. Therefore, it helps stop cyber attackers from entering private networks. These are servers, referred to as “middlemen,” because they connect end users and the web pages they visit online.
When a computer attaches to the internet, it uses an IP address. It is similar to your home street address, which tells incoming data where to go and tags outgoing data with a return address so other devices can authenticate. A proxy server is a processor on the internet with its IP address.
Proxy Server and Network Security
Proxies provide a valued layer of security for your computer. They can be set as a web filter or firewall, protecting your computer from internet threats such as malware.
This extra security is valuable with a secure web gateway or other email security products. This way, you can filter traffic based on its security level or how much traffic your network—or separate computers—can handle.
How to use a proxy? Some people use substitutions for personal purposes, such as hiding their location when watching a movie online. But for companies, they can be used to accomplish several critical tasks, such as:
Improve security
- Secure employees’ internet activities from people trying to snoop on them
- Balance internet traffic to prevent crashes
- Control employee and staff website access in the office
- Save bandwidth by caching files or compression incoming traffic.
How Proxies Work
Because proxy servers have IP addresses, they act as an intermediary between the computer and the internet. Your computer knows this address, and once you send an appeal on the internet, it is routed to a proxy, which then gets a response from the web server and passes data from the page to your computer’s browser, such as Chromium, Safari, Firefox, or Microsoft Edge.
How to Get a Proxy
There are hardware and software versions. Hardware influences sit between your network and the internet, where they receive, send, and forward data from the web. Software proxies are usually hosted by the provider or reside in the cloud. You download and install a request on your computer that facilitates interaction with the proxy.
Often, software proxies can be obtained for a monthly fee. Sometimes, they are free. Free versions offer users fewer addresses and may only cover a few devices, while paid proxies can meet the demands of businesses with many devices.
How are the Server Settings?
To start with a proxy server, you must configure it on your computer, device, or network. Each operating system has its setup procedure, so check the obligatory steps for your computer or network.
However, in most cases, setup means using an automated configuration script. If you want to do this manually, you can enter the appropriate IP address and port.
How Do Proxies Protect Computer Privacy and Data?
Proxy servers perform firewall and filter functions. End users or network administrators can choose proxies to protect data and privacy. It checks data coming in and out of your computer or network. It then smears rules to prevent you from disclosing your digital address. Only the proxy IP address is seen by hackers or other malicious actors. Without your private IP address, people on the internet have no direct access to your data, schedule, apps, or personal files.
With this, web requests go to the proxy, reaching out and getting what you want from the internet. If the server has encryption capabilities, passwords and other personal data get additional protection.
How To Submit Your Articles?
To get your Blog posted on Techitags, you will first have to pitch us a post and showcase your writing skills and knowledge.
You can drop a mail at contact@techitags.com with the subsequent info
Why Write For Techitags – Proxy Write For Us
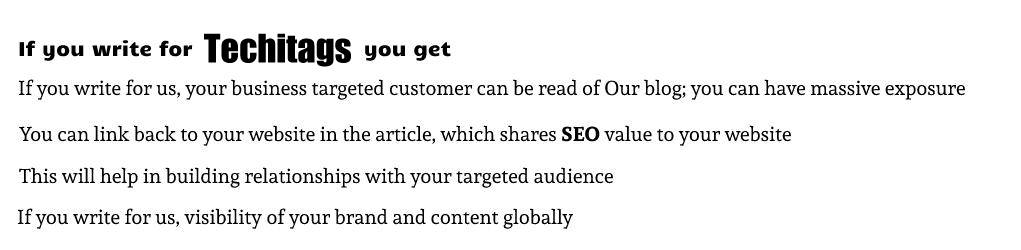
Guidelines For Blog Post
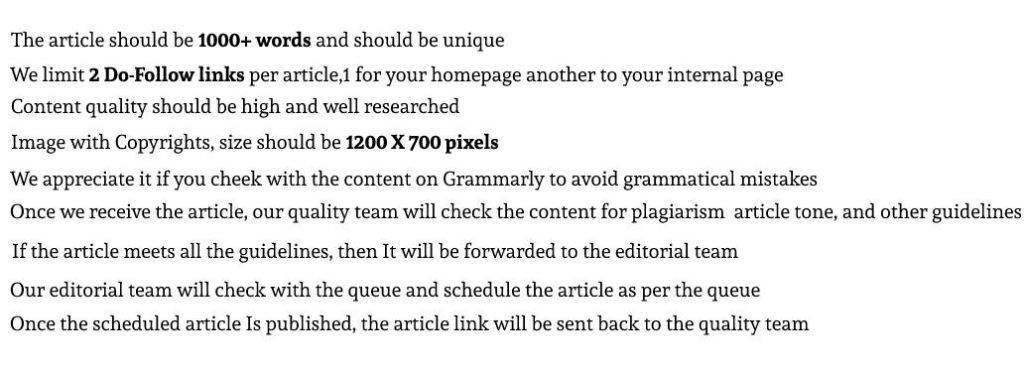
Search Terms Related To Proxy Write For Us
submit an article
contributor guidelines
become a guest blogger
guest posting guidelines
submit article
guest author
looking for guest posts
guest posts wanted
guest post
become guest writer
This post was written by
submit an article
send a tip
write for us
submit post
Search Terms Related To Proxy Write For Us
Proxy “guest post
Proxy “write for us”
Proxy “guest article”
Proxy “guest post opportunities”
Proxy “this is a guest post by”
Proxy “looking for guest posts”
Proxy “contributing writer”
Proxy “want to write for”
Proxy “submit blog post”
Proxy “contribute to our site”
Proxy “guest column”
Proxy “submit Face Book Ads”
Proxy “submit Face Book Ads”
Proxy “This post was written by”
Proxy “guest post courtesy of ”
Proxy “guest posting guidelines”
Proxy “suggest a post”
Proxy “submit an article”
Proxy “contributor guidelines”
Proxy “contributing writer”
Proxy “submit news”
Proxy “submit post”
Proxy “become a guest blogger
Proxy “guest blogger”
Proxy “guest posts wanted”
Proxy “guest posts wanted”
Proxy “guest poster wanted”
Proxy “accepting guest posts”
Proxy “writers wanted”
Proxy “articles wanted”
Proxy “become an author”
Proxy “become guest writer”
Proxy “become a contributor”
Proxy “submit guest post”
Proxy “submit an article”
Proxy “submit article”
Proxy “guest author”
Proxy “send a tip”
Proxy : “guest blogger”
Proxy : “guest post”
Related To Pages
Digital Marketing Write For Us
